Event Storming
The knowledge crunching session has been carried out using the Event Storming approach. It is a workshop-based method where developers and domain experts work together to identify the domain of the project. Using sticky notes with different colors, the method iteratively asks the team members to include different information, such as domain events, commands, and reactions. Finally, the chart with the bounded contexts is produced. All the different steps are highlighted in the following sections.
Unstructured exploration
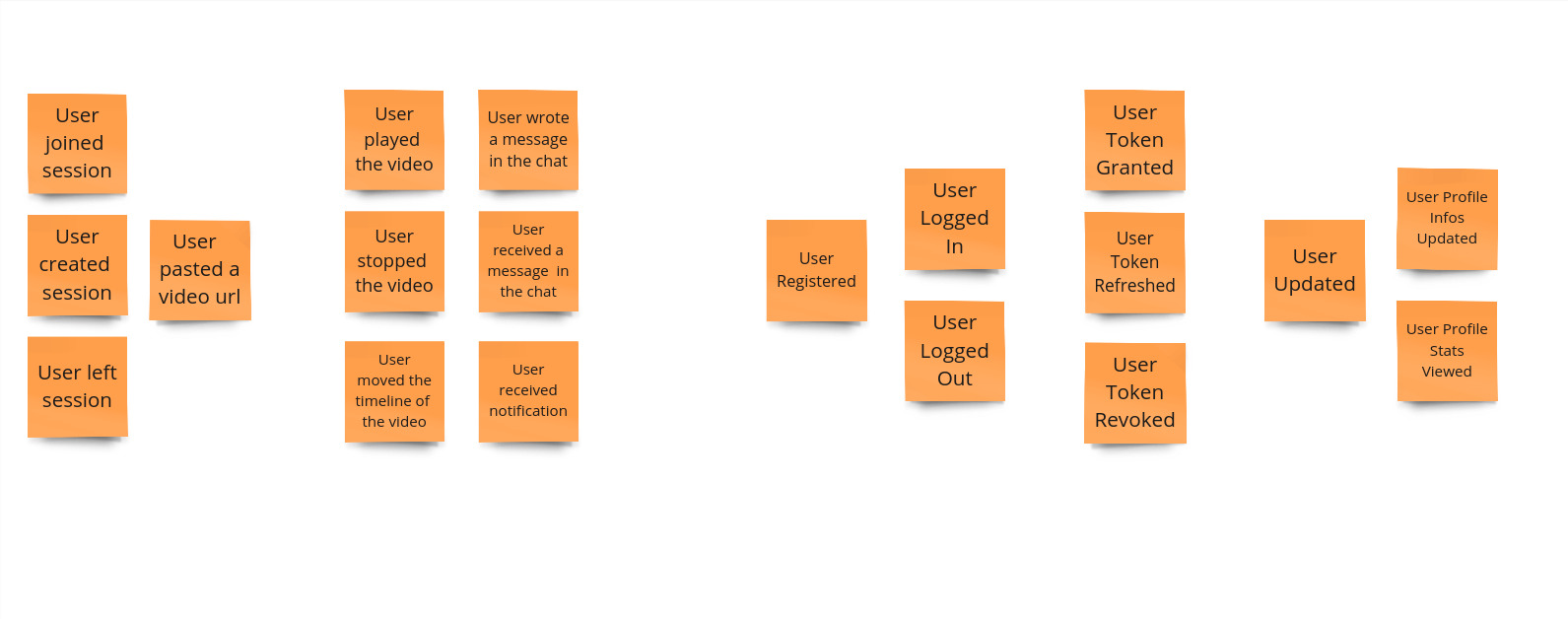
The first step of the Event Storming approach is defining the main domain events that can happen in the system. The sticky notes should be put on a whiteboard, without any specific order.
Timeline
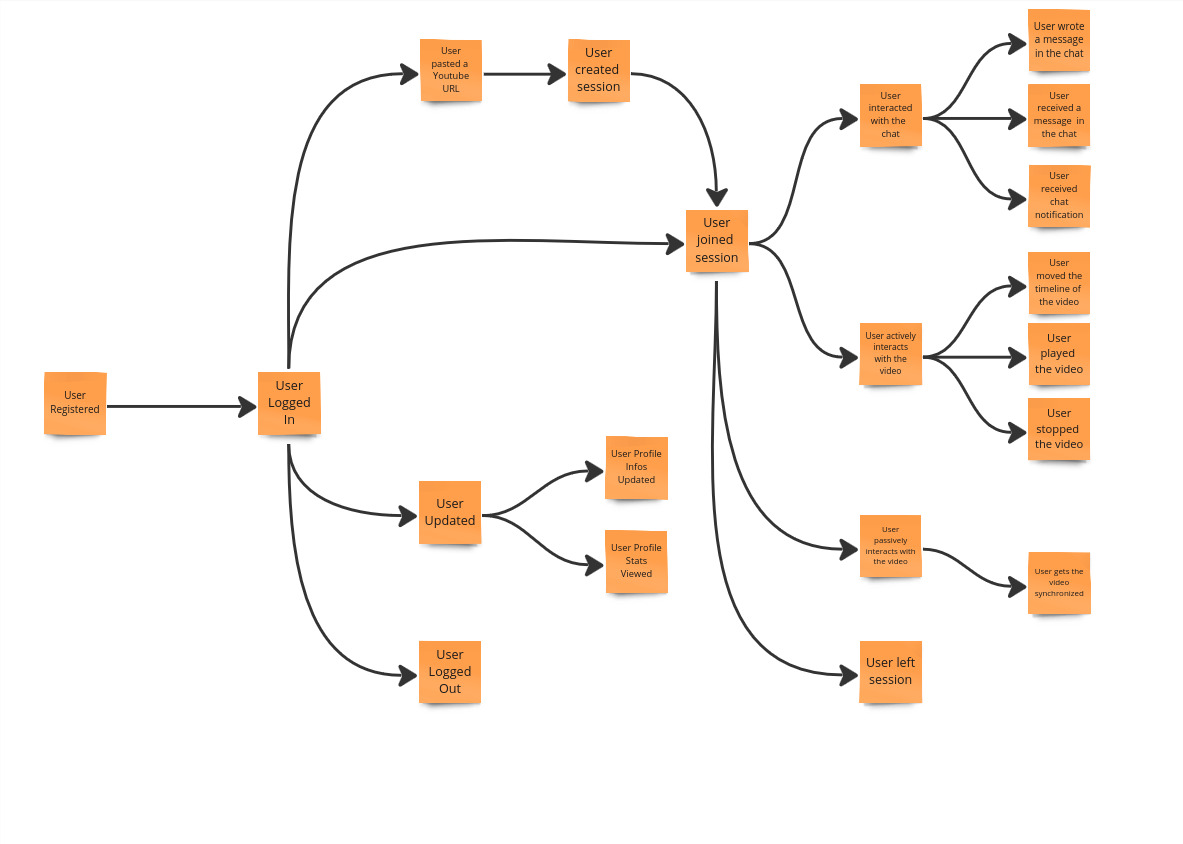
The domain events defined in the previous sections are ordered by time and arrows are drawn to indicate their dependency.
Pain Points
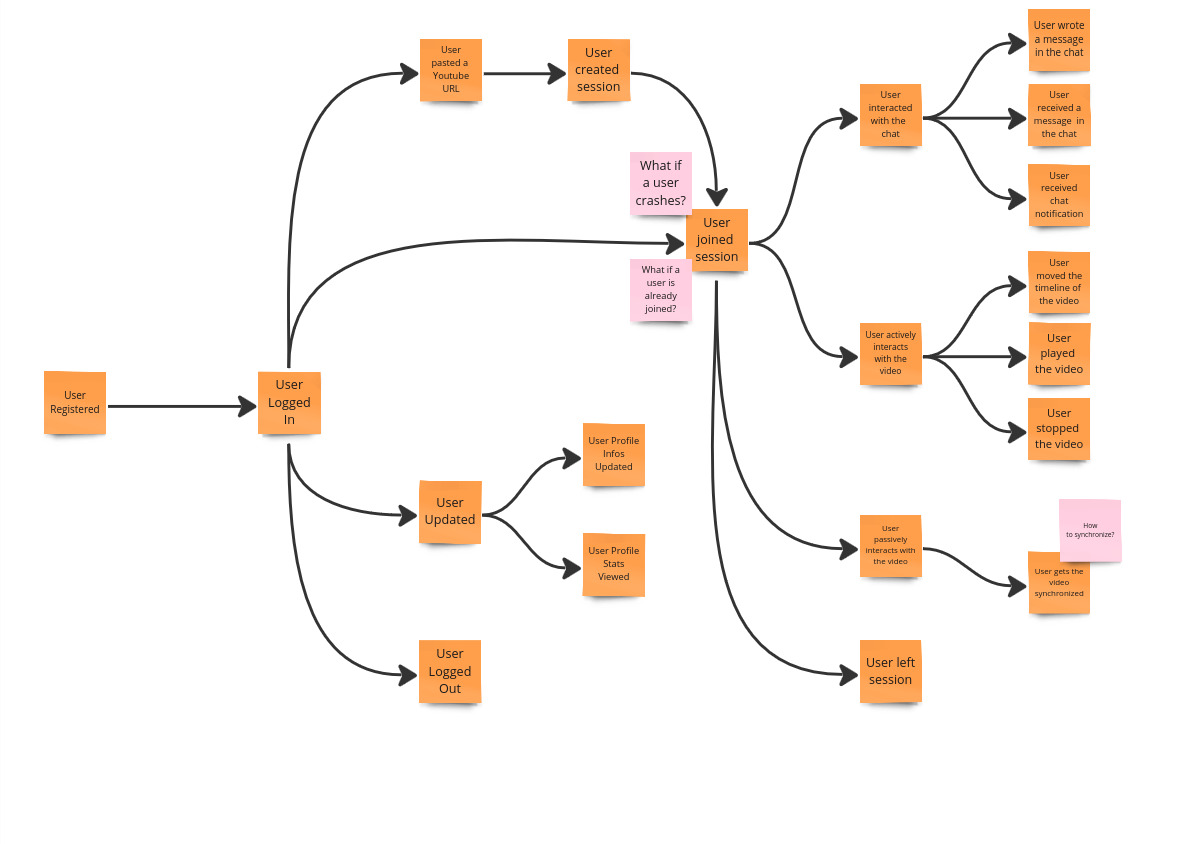
The team members should spot potential problems that can occur in the system and may need special attention.
Pivotal points
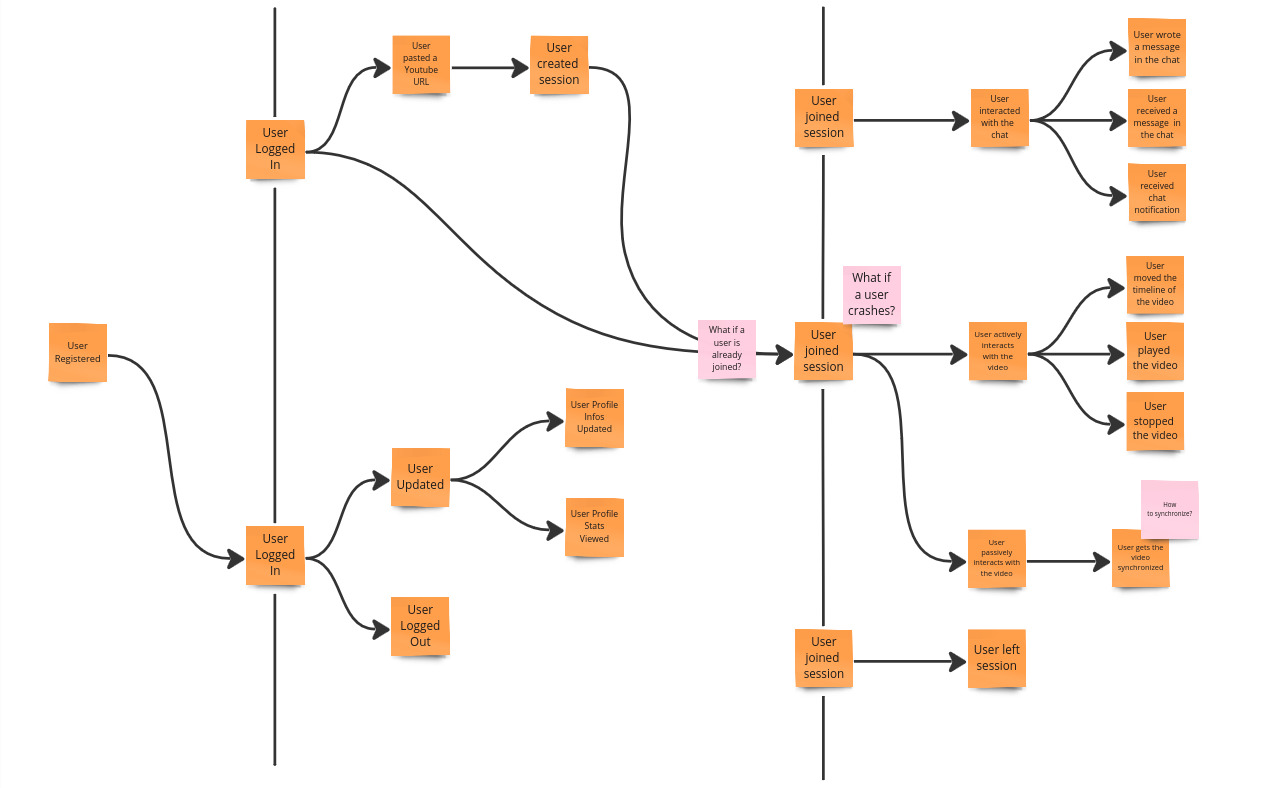
Pivotal points are points where the system could be split into multiple bounded contexts.
Commands
The team identifies the commands that trigger the domain events and their respective actor.
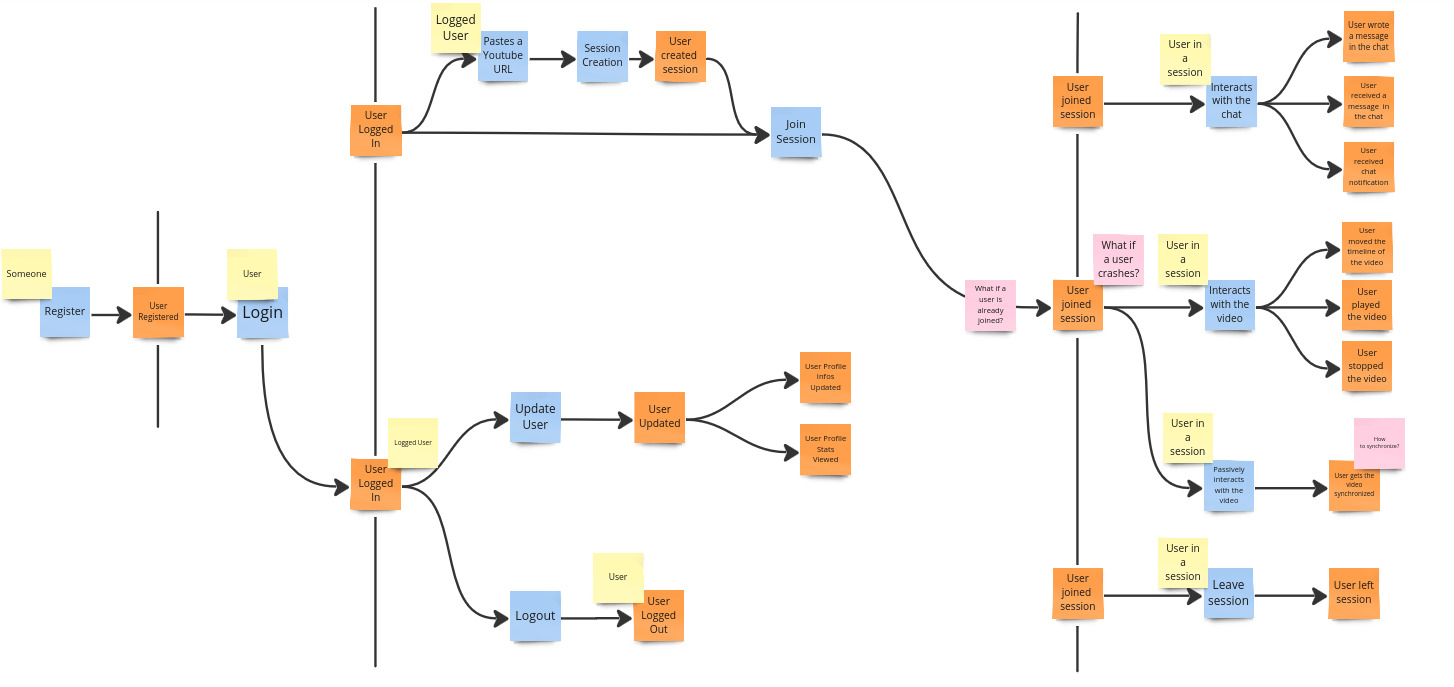
Reactions
Reactions are something that happens when something else happens. They outline actions triggered when an event occurs.
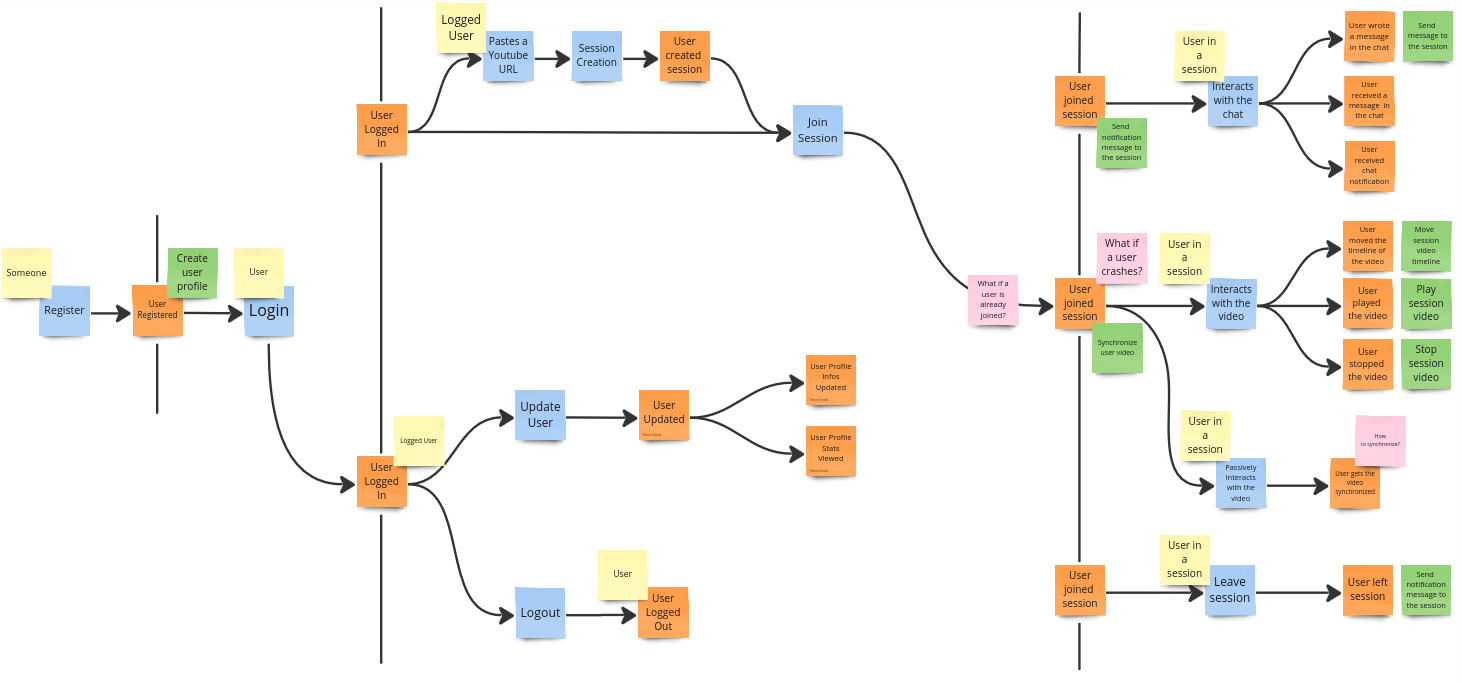
Read models
Read models encompass data that is read in a particular context.
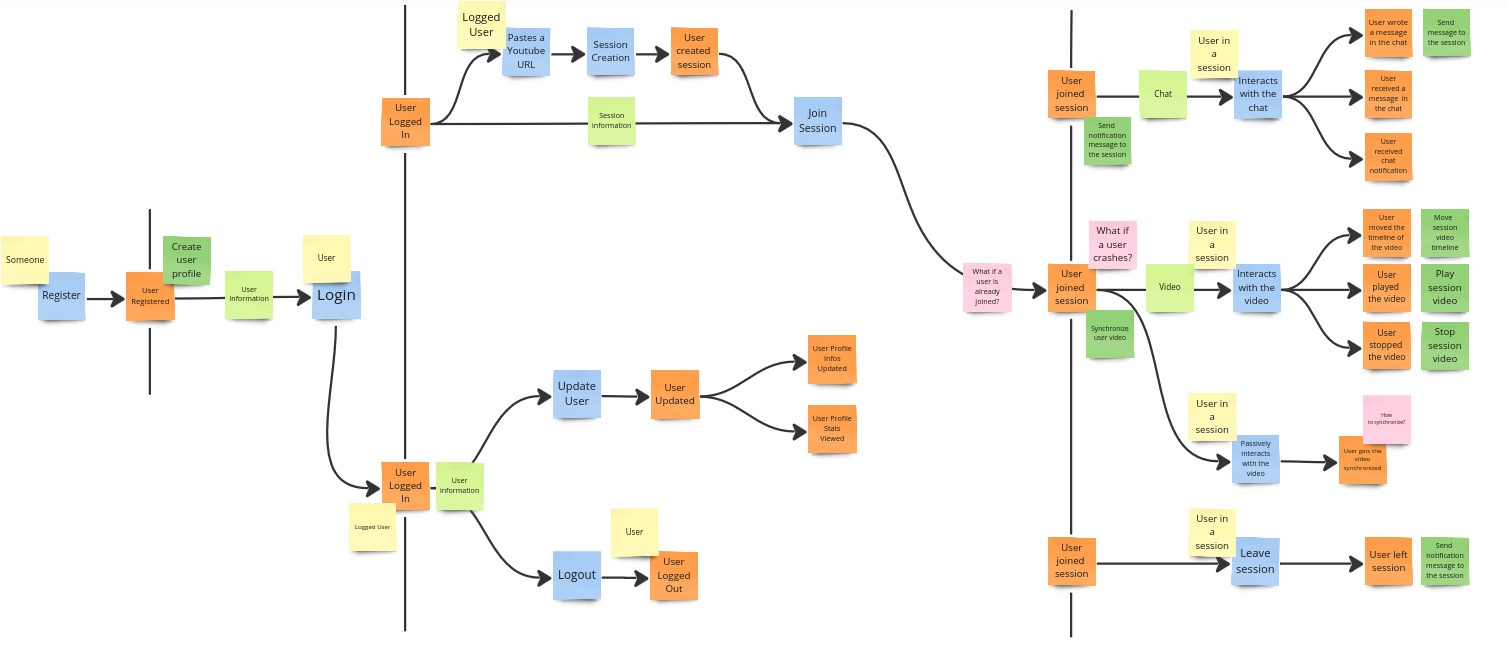
Aggregates
The team members identify the aggregates of the system. They are defined as clusters of domain objects that can be treated as a single unit.
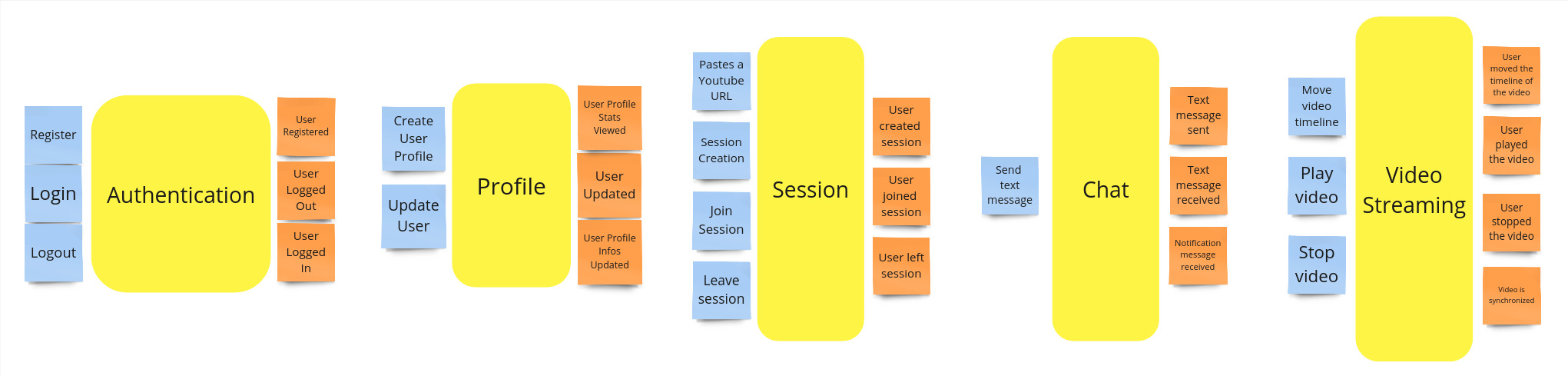
Bounded Contexts
Finally, the bounded contexts of the system are identified. Each one works with its internal representation of the domain. For different bounded contexts, the same concepts may have completely different models. In such cases, a mapping between these models is needed, whenever they should be integrated.
The domain of this project is however rather simple and the separation between the bounded context is complete. This means that they don't share any common concept.
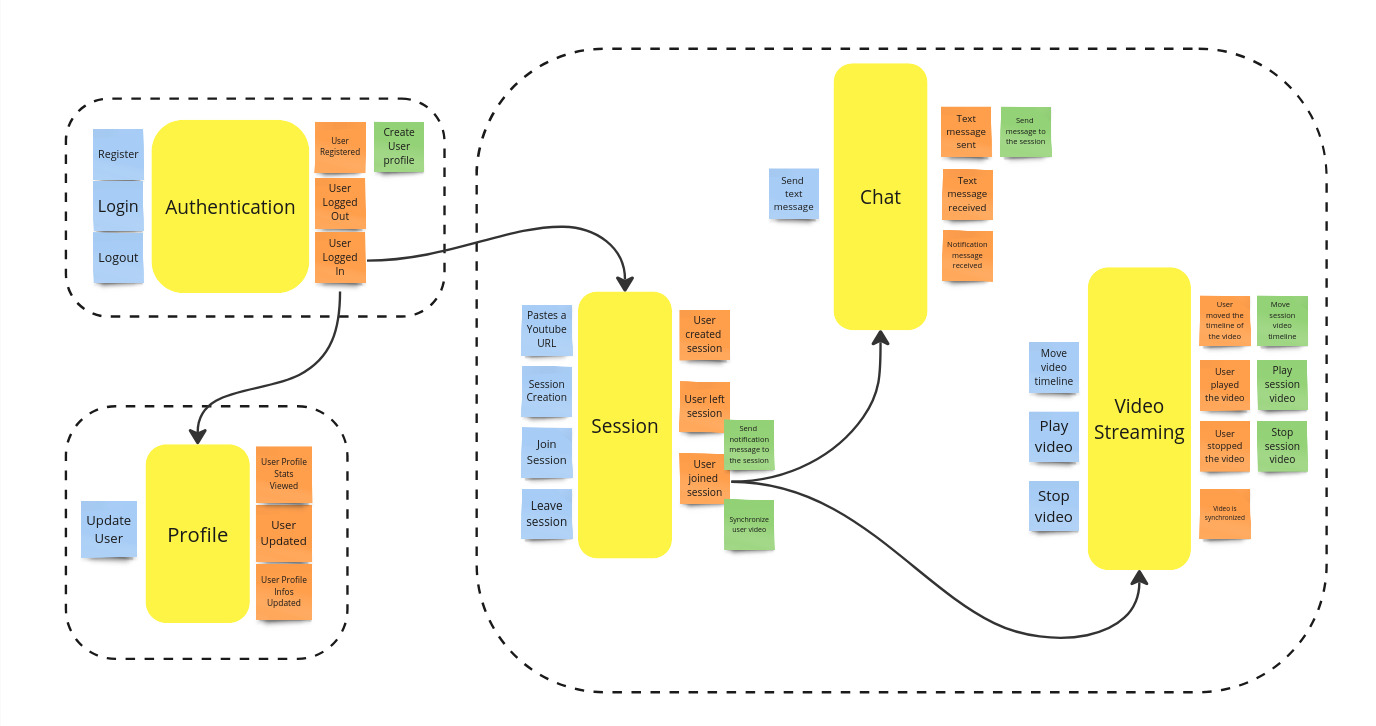
The bounded contexts of the system are:
Auth: manages everything concerning user authentication;Profile: manages everything concerning user profile;Session: manages everything concerning a streaming session.